




 |
 |
 |
 | 13 Signing e-mails | Contents |
 |
In Chapter 11 you learnt more about verifying the authenticity of a public OpenPGP certificate, and signing it with your own private OpenPGP key.
This chapter also explains how to sign a complete e-mail rather than only the certificate. That means applying a digital signature to the e-mail - which is a form of an electronic seal.
"Sealed" in this way, the text can still be read by everyone, but it allows the recipient to find out whether the e-mail was manipulated or modified during delivery. The signature tells the recipient that the message is really from you. And: If you are corresponding with someone whose public certificate you do not have (for whatever reason), you can at least "seal" the message with your own private key.
You have probably noticed that this digital signature is not identical to an e-mail "signature", which is sometimes included at the end of an e-mail and includes such items as telephone number, address and website. While these e-mail signatures simply function as a type of business card, a digital signature will protect your e-mail from manipulation and clearly confirms the sender.
Besides, a digital signature cannot be compared with a qualified electronic signature, as it went into effect as part of the Signature Act (22 May 2001). However, it serves exactly the same purpose for private or professional e-mail communication.

In fact, signing an e-mail is even easier than encrypting it (see Chapter 12). Once you have composed a new e-mail, go through the following steps - similar to the encryption process:
These steps are described in detail on the following pages.
First, compose a new e-mail in Outlook and address it to the person you are writing to.
Before you send your message, tell the system that your message should be sent with a signature: To do this, activate the button with the signature pen or the menu item Format -> Sign message.
Your e-mail window would then look something like this:
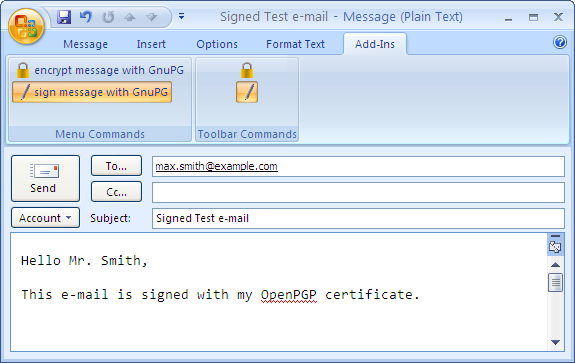
Now click on [Send].
Just as is the case for encrypting e-mails, Gpg4win automatically detects the protocol - OpenPGP or S/MIME - for which your own certificate (with the private key for signing) is available.
If you have your own OpenPGP and S/MIME certificate with the same e-mail address, Kleopatra will ask you to select a protocol before the e-mail is signed:
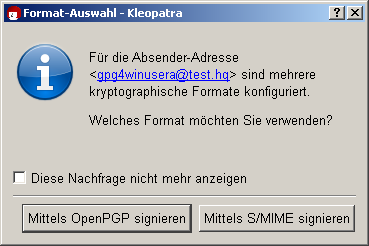
If you have several certificates (e.g. two OpenPGP certificates for the same e-mail address) for the selected method,Kleopatra will open a window which displays your certificates (here: OpenPGP), each with its own private key:
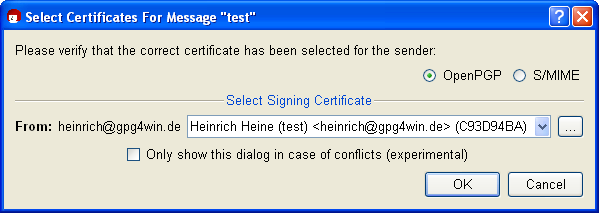
Confirm your selection with [OK].
In order to complete the signing process for your e-mail, you will be asked to enter your secret passphrase in the following pin entry window:
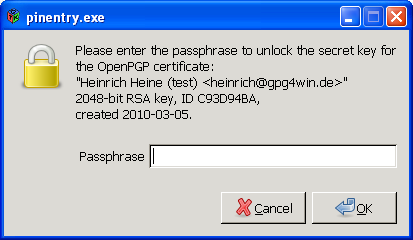
This is required because:
It makes sense, because only your own private key confirms your identity. The person you are corresponding with can then check your identity using your public certificate, which he already has or can obtain. Because only your private key matches your public certificate.
Confirm your passphrase entry with [OK]. Your message is now signed and sent.
Once your message has been signed successfully, the following dialog appears:
Congratulations! You have encrypted your first e-mail!
You have learnt how to sign an e-mail using your own certificate - which contains your private key.
You know how to encrypt an e-mail using the public certificate of the person you are writing to.
Now you are familiar with the two most important techniques for sending secure e-mails: encryption and signatures.
Of course you can also combine the two techniques. From now on, eacht time you send an e-mail, think about how you want to send it - depending on the importance and required level of protection for your e-mail:
You can use these four combinations with either OpenPGP or S/MIME.
Let's assume you have received a signed e-mail from the person you are corresponding with.
It is very easy to check this digital signature. All you need is the public OpenPGP or X.509 certificate of your correspondence partner. You should have already imported his public certificate into your certificate administration prior to performing this check (see Chapter 10).
To check a signed OpenPGP or S/MIME e-mail, proceed as you would for decrypting an e-mail (see Chapter 9):
Start Outlook and open a signed e-mail.
GpgOL will automatically transfer the e-mail to Kleopatra for a signature check. Kleopatra will report the result in a status dialog, e.g.:
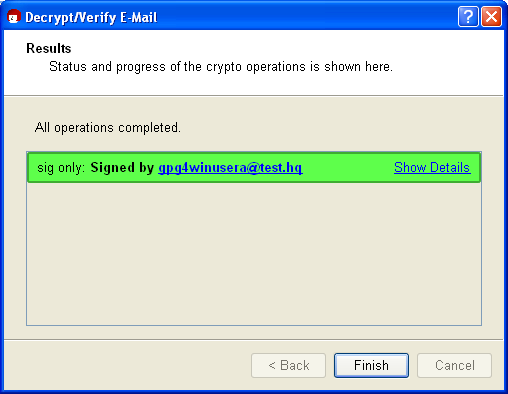
The signature check was successful! Now close to the dialog in order to read the signed e-mail.
If you want to perform the check again manually, select Extras -> Decrypt/Check GpgOL in the menu of the open e-mail.
If the signature check is not successful, it means that the message was changed during the delivery process. Because of the technical nature of the Internet, it is possible that the e-mail was unintentionally modified because of a defective transmission. That is probably the most likely cause. However, it can also mean that the text was changed intentionally.
Section 13.3 has information on how to proceed in such a case.
There are several reasons for a broken signature:
If you receive the message "Bad signature" or "Check failed", it is a warning that your e-mail may have been manipulated! That means that it is possible that someone changed the e-mail's contents or the subject line.
At the same time, a broken signature does not necessarily mean that the e-mail was manipulated. It is also possible that the e-mail was modified due to a defective transmission.
In any case, you should always take a broken signature seriously and
ask the sender to resend the e-mail!
It is recommended that you set your program to only send e-mails in
"text" format and not in "HTML" format. However, if you
decide to use HTML for signed or encrypted e-mails, it is possible
that formatting information will be lost by the time it reaches the
recipient, which can result in a broken signature.
In Outlook 2003 and 2007, you can set the message format to Text only in Extras -> Options -> E-Mail Format.
You know: A message is usually encrypted using the public certificate of your correspondence partner, who then decrypts the e-mail using his private key.
The reverse possibility - encryption with a private key - does not make sense, since the whole world knows the associated public certificate and could then decrypt the message.
However, as you have already seen in this chapter, there is still another method to create a file using your private key - namely the signature.
A digital signature confirms the author - because if someone successfully applies your public certificate to this file (the signature), this file could only have been encoded by your private key. And only you can have access to this key.
You can combine both options, namely encrypting and signing the e-mail:
This means that the message has two security characteristics:
Your correspondence partner opens the outer strong envelope with his own private key. This ensures secrecy, because only this key can be used to decode the text. He reads the seal with your public certificate, which proves that you were the author, because if your public certificate matches, the seal (digital signature) can only have been encoded with your private key.
It is pretty tricky when you think about it, but also very simple.
© 31. August 2010, v3.0.0-beta1 (last minor changes from 21. September 2010)
The Gpg4win Compendium is filed under the
GNU Free Documentation License v1.2.
 |
 |
 |
 | 13 Signing e-mails | Contents |
 |