




 |
 |
 |
 | 8 Distribution of public certificates | Contents |
 |
When using Gpg4win on a daily basis, it is very practical that for the purpose of encrypting and checking signatures you are always dealing with "public" certificates which only contain public keys. As long as your own secret key and the passphrase which protects it are secure, you have already gone a long way towards ensuring secrecy.
Everyone can and should have your public certificate, and you can and should have the public certificates of your correspondence partners - the more, the better.
Because:
To exchange secure e-mails, both partners must have and use the public certificate of the other person. Of course the recipient will also require a program capable of handling certificates - such as the Gpg4win software package with Kleopatra certification administration.
Therefore, if you want to send encrypted e-mails to someone, you must have their public certificate to encrypt the e-mail.
In turn, if someone wants to send you encrypted e-mails, he must have your public certificate and use it for encryption purposes.
For this reason you should now allow access to your public certificate.
Depending on how many people you corespond with, and which certificate format you are using, you have several options. For example, you can distribute your public certificate ...
Let's look at the first two variants on the following pages.
Do you wish to make your public certificate accessible to the person
you are corresponding with? Simply send them your exported public
certificate per e-mail. This section will show you how this
works.
Practice this process with your public OpenPGP certificate! Adele can
assist you. The following exercises only apply to OpenPGP; for
information on publishing public X.509 certificates, please see
page X.
Adele is a very nice e-mail robot which you can use to practice correspondence. Because it is usually more pleasant to correspond with a smart human being rather than a piece of software (which is what Adele is, after all), you can imagine Adele this way:

First, send Adele your public OpenPGP certificate. Using the public key in this certificate, Adele will send an encrypted e-mail back to you.
You then use your own secret key to decrypt Adele's response. To be able to respond to Adele with an encrypted e-mail, Adele has attached her own public certificate.
Adele acts just like a real person you are corresponding with. Of course, Adele's e-mails are not nearly as interesting as those from the people you are actually corresponding with. On the other hand, you can use Adele to practice as much as you like - which a real person might find bothersome after a while.
So, now you export your public OpenPGP certificate and send it via e-mail to Adele. The following pages how how this works.
Select the public certificate to be exported in Kleopatra (by clicking on the corresponding line in the list of certificates) and then click on File -> Export certificates... in the menu. Select a suitable file folder on your PC and save the public certificate with the file type.asc e.g.: mein-OpenPGP-Zertifikat.asc. The other file types, which can be selected, .gpg or.pgp, will save your certificate in binary format. That means that in contrast to an .ascfile, they cannot be read in the text editor.
When you select the menu item, please make sure that you are only exporting your public certificate - and not the certificate of your entire key pair with the associated private key by mistake.
Review the file once more by selecting Windows Explorer and selecting the same folder that you indicated for the export.
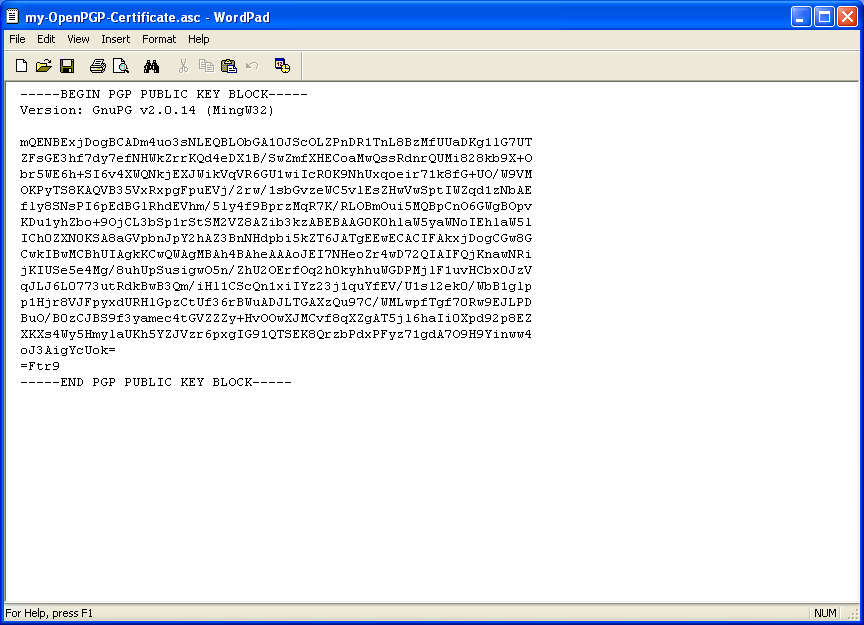
Now open the exported certificate file with a text editor, e.g. WordPad. The text editor will display your public OpenPGP certificate as it really looks - a fairly confusing block of text and numbers:
When publishing your OpenPGP certificate by e-mail, there are two variants which can take into account whether an e-mail program can send attachments.
This option always works, even if you are not able to attach files -
as may be the case with some e-mail services on the Web.
Also,
it is a way of seeing your public certificate for the first time,
knowing exactly what is behind it, and what the certificate actually
consists of.
Highlight the entire public certificate in the text editor from
---BEGIN PGP PUBLIC KEY BLOCK---
up to
---END PGP PUBLIC KEY BLOCK---
and copy it with the menu command or the key shortcut Strg+C. Now you have copied the certificate in the memory of your computer (Clipboard in a Windows context).
Now you can start your e-mail program - it does not matter which one you use - and add your public certificate into an empty e-mail. In Windows, the key command for adding ("Paste") is Strg+V. You may know this process - copying and pasting - as "Copy & Paste".
The e-mail program should be set up in such a way that it is possible to send only text messages and not HTML formated messages (see Section 13.3 and Annex 25.4).
Now address this e-mail to adele@gnupp.de and write something in the subject line e.g. My public OpenPGP certificate.
This is approximately what your e-mail will look like:
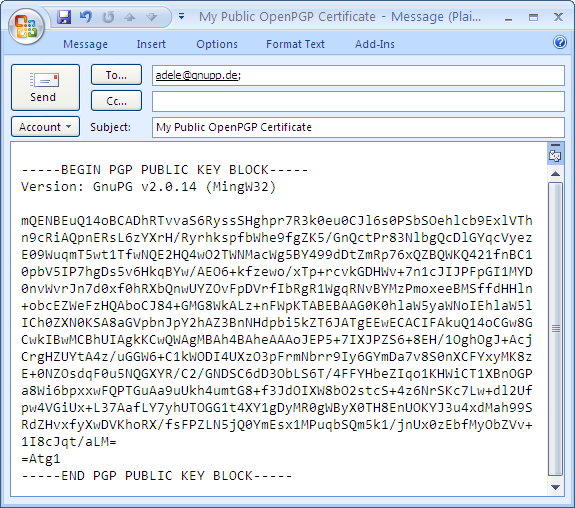
Now send the e-mail to Adele. Make sure to include your own e-mail address as the sender. Otherwise you will never receive Adele's response ...
As an alternate to Variant 1, you can also send your exported public OpenPGP certificate directly as an e-mail file attachment. This is often the simpler and more commonly used method. Above, you learnt about the "Copy & Paste" method, because it is more transparent and easier to understand.
Now write another e-mail to Adele - this time with the certificate file in the attachment:
Add the previously exported certificate file as an attachment to your new e-mail - just as you would for any other file (e.g. pulling the file into the emtpy e-mailwindow). Add the recipient (adele@gnupp.de) and a subject, e.g.: My public OpenPGP certificate - as a file attachment.
Of course you can also add a few explanatory sentences. However, Adele does not need this explanations, because her only purpose is to help you practice this process.
Your finished e-mail should look something like this:
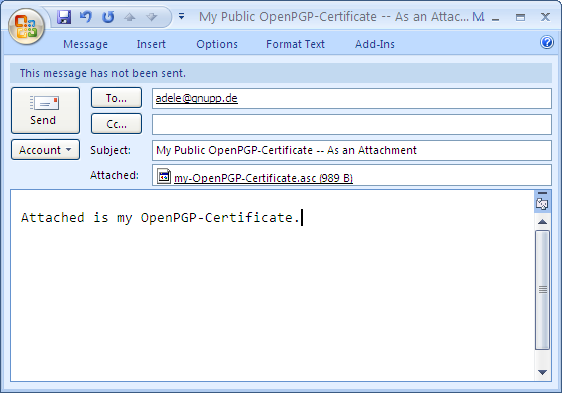
Now send the e-mail and attachment to Adele.
You have exported your public OpenPGP certificate in Kleopatra into a file. Subsequently, you have also copied the content of the file directly into an e-mail and attached the complete file as an e-mailattachment. Both e-mails have been sent to someone else - in this case, to Adele.
The same process applies if you are sending your public certificate to a real e-mail address. Usually, you should send public certificates as a file attachment, as described in Variant 2. This is the easiest way to do it, both for you and the recipient. And it also has the advantage that your recipient can import your certificate file directly into his own certificate administration (e.g. Kleopatra).
Please note: You can only distribute your OpenPGP certificate via an OpenPGP certificate server.
Publishing your public OpenPGP certificate on a public certificate server is always a good idea, even if you are only exchanging encrypted e-mails with just a few people. This way, your public certificate is accessible to everyone on an Internet server. This saves you time in having to send your certificate e-mail to all of the people you are corresponding with.
At the same time, publishing your e-mail address on a certificate server can also make your e-mail address more susceptible to spam. This can only be addressed with good spam protection.
This is how it works: Select your public OpenPGP certificate in Kleopatra
and click on File -> Export certificate to server....
If you have not defined a certificate server, you will see a warning:
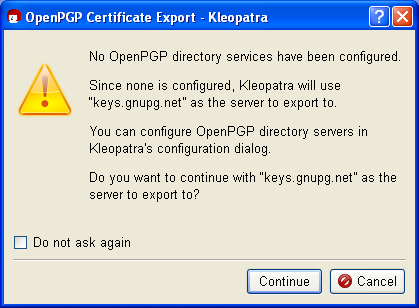
The public OpenPGP certificate server already contains keys.gnupg.net default settings. Click on [Continue] to send your selected public certificate to this server. There, your public certificate is distributed to all globally connected certificate servers. Anyone can download your public certificate from one of these OpenPGP certificate servers and use it send you a secure e-mail.
If you are only testing this process, please do not send the practice certificate: In the top dialog, click on [Cancel]. The test certificate is worthless and cannot be removed by the certificate server. You would not believe how many test certificates with names like "Julius Caesar", "Helmut Kohl" or "Bill Clinton" are already floating around on these servers ...
Now you know how to publish your public OpenPGP certificate on an OpenPGP certificate server on the Internet.
For information on how to search for the public OpenPGP certificate of people you are corresponding with on a certificate server, see Chapter 16. You can read this chapter now or later when you need this function.
In the case of public X.509 certificates, this process is even easier: all you need to do is to send a signed S/MIME e-mail to the person you are corresponding with. Your public X.509 certificate is contained in this signature, and can be imported into the recipient's certificate administration.
Unfortunately, you cannot use Adele to practice X.509 certificates since the robot only supports OpenPGP. Therefore you should pick another person to write you, or alternately write to yourself.
Some public X.509 certificates are distributed by the certificate authority. This is usually done using X.509 certificate servers, which however do not synchronize on a global basis, as is the case with OpenPGP key servers.
When you export your public X.509 certificate, you can highlight the entire public certificate chain and save it in a file - generally the root certificate, CA certificate and personal certificate - or only your public certificate.
The first is recommended since the person you are corresponding with may be missing some parts of the chain, which he otherwise would have to find. To do this, click on all elements of the certificate chain in Kleopatra while holding the Shift key, and export the highlighted certificate into a file.
If the person you are corresponding with does not have the root certificate, he must indicate that he trusts it, or have an administrator do so, in order to finally also trust you. If this has already been done (e.g. because they are both part of the same "root"), then this shiop is already in place.
© 31. August 2010, v3.0.0-beta1 (last minor changes from 21. September 2010)
The Gpg4win Compendium is filed under the
GNU Free Documentation License v1.2.
 |
 |
 |
 | 8 Distribution of public certificates | Contents |
 |